
Hey! Welcome to another one of our blogs on the configuration of the new series of WLC from Cisco the C9800! In this post, I want to go through with you an issue that I ran into when configuring a Guest SSID which was using MAB with a CWA to redirect to a portal on […]

Hey! A quick short blog on some internal DHCP configuration for the C9800 WLC! As we are starting to implement the new generation of the wireless controller for customers, we anticipate that we will stumble over a few gotchas with config and plan to share through short blogs with you guys to hopefully save you […]
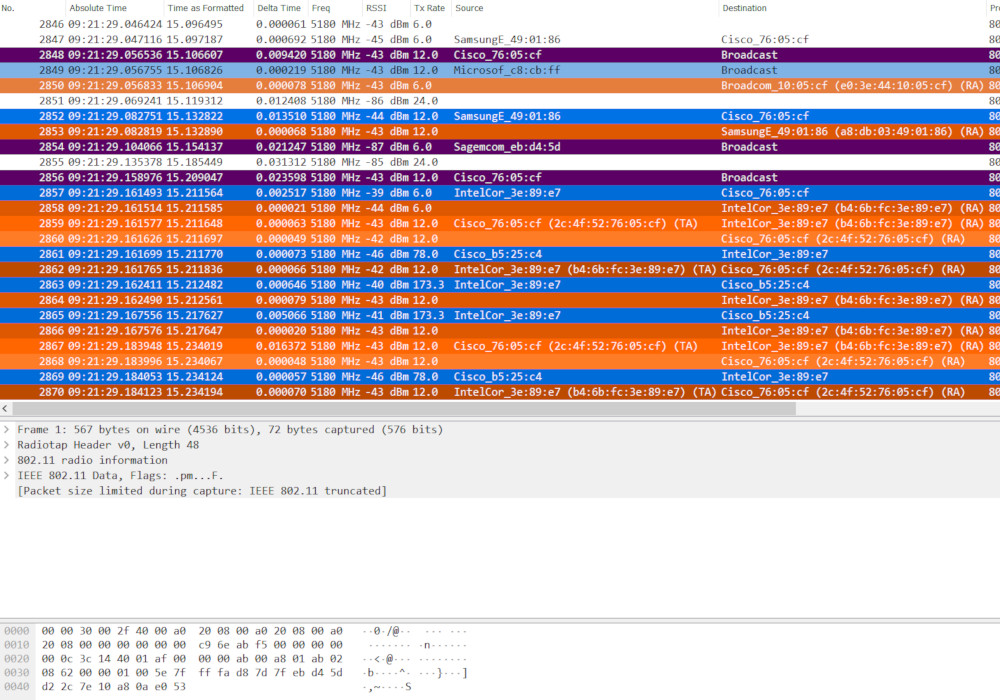
Both Mac & Matt are currently studying for their final CWNP exam – CWAP! And have been making notes and tips along the way so we wanted to share some with you guys. A lot of these Wireshark filters below we got from the guys over at CTS but we have added a few more […]

So you have just deployed your new shiny Cisco WLCs and you have been waiting for weeks for the cablers to install your APs as per your design and you are sitting there all excited as you can finally enable the switch ports that the APs are connected to but… Oh no, no APs are […]



