
Hey!
Welcome to another one of our Cisco C9800 configuration blogs!
This time we will be covering Local Web Authentication (LWA), where guest sessions are managed by the WLC itself.
We can authenticate against RADIUS, TACACS, LDAP or local WLC Guest Users database. In this guide we will use local WLC Guest Users.
As I was preparing for deployment for a customer that would be using 2 x foreign C9800CLs in HA SSO & 2 x anchor C9800CLs in HA SSO I had my lab set up in this configuration also. In this scenario, the WLAN that I will be using is being guest anchored via a tunnel from the foreign WLC to the Anchor.
This meant that all the configuration you see below had to be replicated across both the foreign and the anchor WLCs.
We will include the steps we used from the official Cisco config guide but will add screenshots from our lab WLCs to hopefully make it a bit easier to follow.
Official Cisco guide:
Below are the steps to configure LWA.
Procedure
| Step 1 | Choose Configuration > Security > AAA. |
| Step 2 | In the Authentication section, click Add. |
| Step 3 | In the Quick Setup: AAA Authentication window that is displayed, enter a name for your method list. |
| Step 4 | Choose the type of authentication you want to perform before allowing access to the network, in the Type drop-down list. |
| Step 5 | Choose if you want to assign a group of servers as your access server, or if you want to use a local server to authenticate access, from the Group Type drop-down list. |
| Step 6 | To configure a local server to act as a fallback method when servers in the group are unavailable, check the Fallback to local checkbox. |
| Step 7 | Choose the server groups you want to use to authenticate access to your network, from the Available Server Groups list and click > icon to move them to the Assigned Server Groups list. |
| Step 8 | Click Save & Apply to Device. |
As we are using local WLC Guest Users database to authenticate against, we will specify ‘local‘ Group type for ‘login‘.
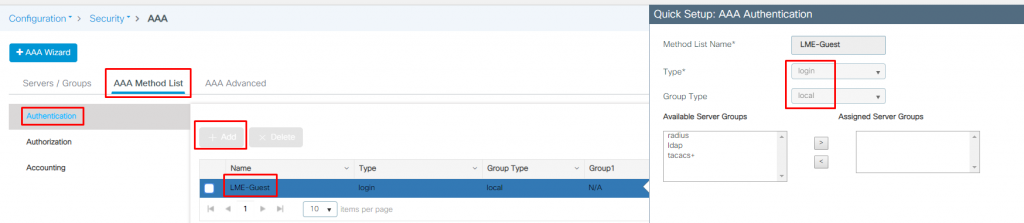
Procedure
| 1 | Choose Configuration > Security > Web Auth. |
| 2 | On the Web Auth page, click Add. |
| 3 | In the Create Web Auth Parameter window that is displayed, enter a name for the parameter map. |
| 4 | In the Maximum HTTP Connections field, enter the maximum number of HTTP connections that you want to allow. |
| 5 | In the Init-State Timeout field, enter the time after which the init state timer should expire due to the user’s failure to enter valid credentials on the login page. |
| 6 | Choose the type of Web Auth parameter. |
| 7 | Click Apply to Device. |
| 8 | On the Web Auth page, click the name of the parameter map. |
| 9 | In the Edit WebAuth Parameter window that is displayed, choose the required Banner Type. If you choose Banner Text, enter the required banner text to be displayed. If you choose File Name, specify the path of the file from which the banner text has to be picked up. |
| 10 | Enter the virtual IP addresses as required. |
| 11 | Set appropriate status of WebAuth Intercept HTTPS, Captive Bypass Portal, and Watch List Enable. |
| 12 | In the Watch List Expiry Timeout field, enter the time in seconds after which the watch list should time out. |
| 13 | Set appropriate status for Disable Success Window, Disable Logout Window, and Login Auth Bypass for FQDN. |
| 14 | Check the Sleeping Client Status checkbox to enable authentication of sleeping clients and then specify the Sleeping Client Timeout in minutes. The valid range is between 10 minutes and 43200 minutes. |
| 15 | Click the Advanced tab. |
| 16 | In the Redirect for log-in field, enter the name of the external server to send a login request. |
| 17 | In the Redirect On-Success field, enter the name of the external server to redirect after a successful login. |
| 18 | In the Redirect On-Failure field, enter the name of the external server to redirect after a login failure. |
| 19 | To configure external local web authentication, perform these tasks: Under Redirect to External Server in the Redirect Append for AP MAC Address field, enter the AP MAC address. In the Redirect Append for Client MAC Address field, enter the client MAC address. In the Redirect Append for WLAN SSID field, enter the WLAN SSID. In the Portal IPV4 Address field, enter the IPv4 address of the portal to send redirects. In the Portal IPV6 Address field, enter the IPv6 address of the portal to send redirects, if IPv6 address is used. |
| 20 | To configure customized local web authentication, perform these tasks: Under Customized Page, specify the following pages: Login Failed Page Login Page Logout Page Login Successful Page |
| 21 | Click Update & Apply. |
Here you can choose a certificate that you want to present guests with when they hit the Captive Portal:

Normally, we would want to have a cert signed by a trusted public CA, but since we don’t have one we won’t select anything in the ‘Trustpoint’ field.
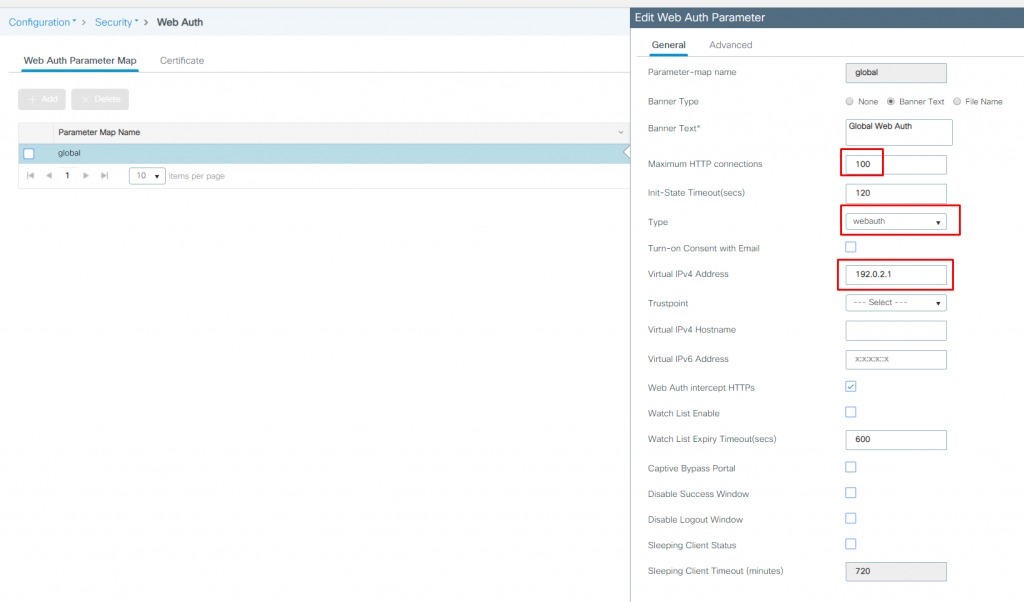
Another thing to point out here is that the Virtual IPv4 Address and Trustpoint certificate must be specified in the global Web Auth Parameter Map. Adding new map won’t even have that options.
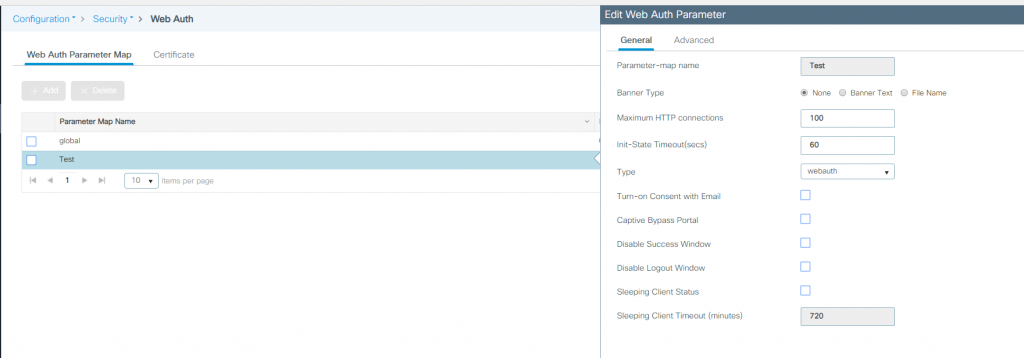
For simplicity, we have just used ‘global‘ Web Auth Parameter Map.
Follow the procedure given below to configure WLAN using web auth security and map the authentication list and parameter map:
Procedure
| Command or Action | Purpose | |
| 1 | enable Example: Device> enable | Enables privileged EXEC mode. Enter your password if prompted. |
| 2 | configure terminal Example: Device# configure terminal | Enters global configuration mode. |
| 3 | wlan profile-name wlan-id ssid-name Example: Device(config)# wlan mywlan 34 mywlan-ssid | Specifies the WLAN name and ID. profile-name is the WLAN name which can contain 32 alphanumeric characters. wlan-id is the wireless LAN identifier. The valid range is from 1 to 512. ssid-name is the SSID which can contain 32 alphanumeric characters. |
| 4 | no security wpa Example: Device(config-wlan)# no security wpa | Disables the WPA security. |
| 5 |
security
web-auth {authentication-list authentication-list-name | parameter-map parameter-map-name}
Example:
Device(config-wlan)# security web-auth authentication-list webauthlistlocal Device(config-wlan)# security web-auth parameter-map sample | Enables web authentication for WLAN.Here, authentication-list authentication-list-name : Sets the authentication list for IEEE 802.1x. parameter-map parameter-map-name : Configures the parameter map. Note When security web-auth is enabled, you get to map the default authentication-list and global parameter-map . This is applicable for authentication-list and parameter-map that are not explicitly mentioned. |
| 6 |
end
Example:
Device(config)# end | Returns to privileged EXEC mode. |
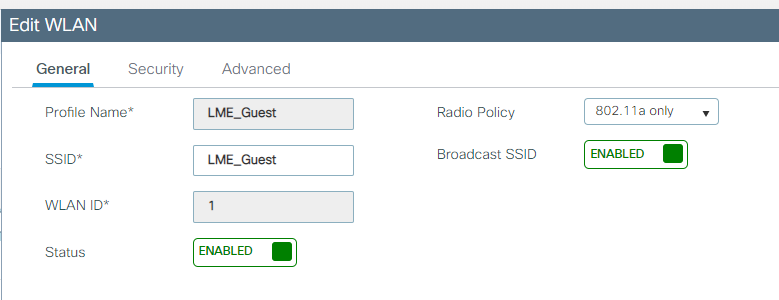
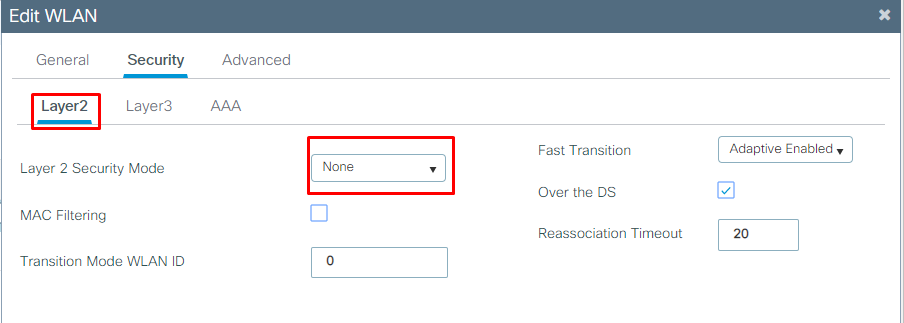
Layer 2 security we will select none here:
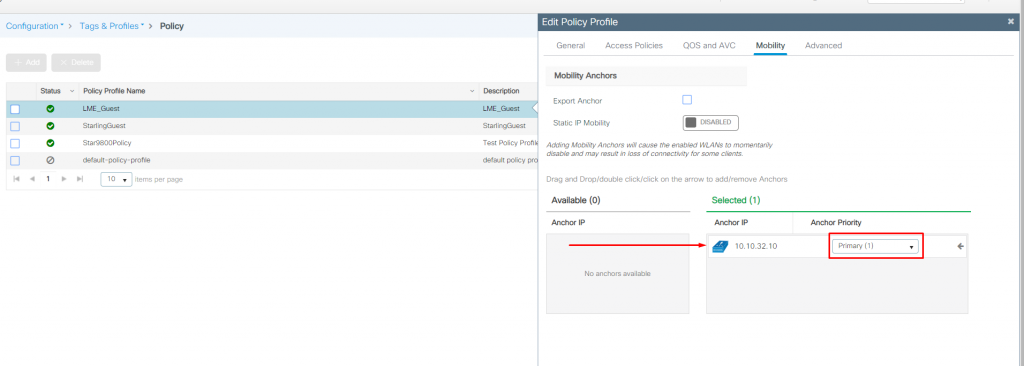
Foreign WLC policy to Anchor the SSID:
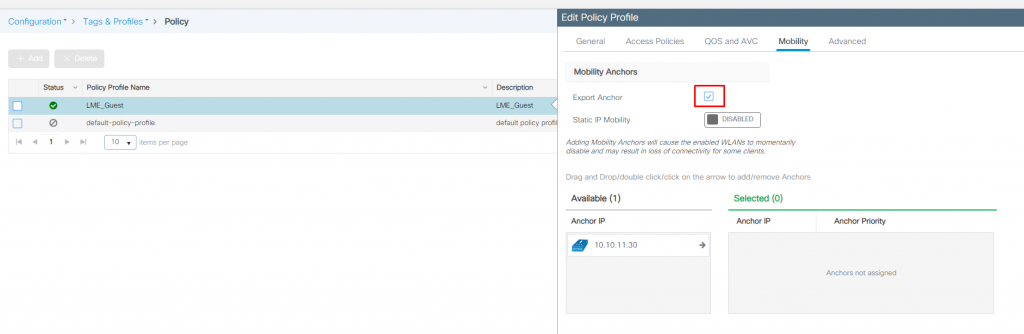
Anchor WLC policy for the SSID:
Before you begin
Ensure that you have configured an access control list (ACL) and a WLAN.
Procedure
| Step 1 | Choose Configuration > Tags & Profiles > WLANs. |
| Step 2 | Click the name of the WLAN. |
| Step 3 | In the Edit WLAN window, click the Security tab and then click the Layer3 tab. |
| Step 4 | Click Show Advanced Settings. |
| Step 5 | In the Preauthenticaion ACL section, choose the appropriate ACL to be mapped to the WLAN. |
| Step 6 | Click Update & Apply to Device. |
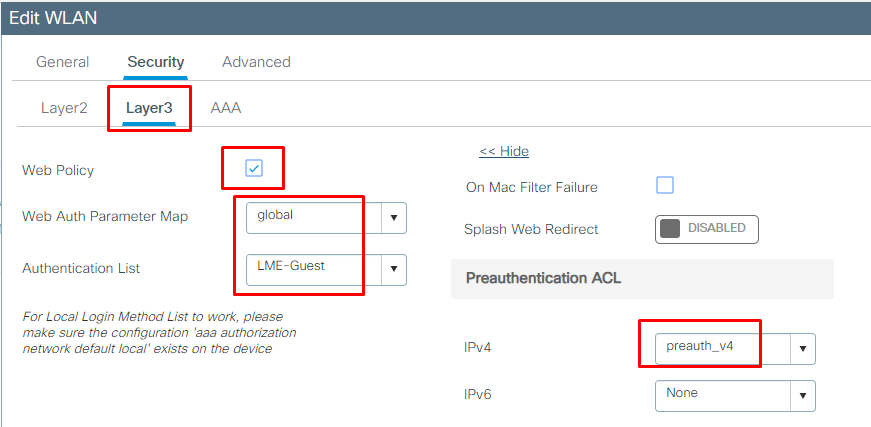
We use the pre-auth ACL here that only allows guests access to DNS and DHCP while blocking access to the network until they have authenticated.
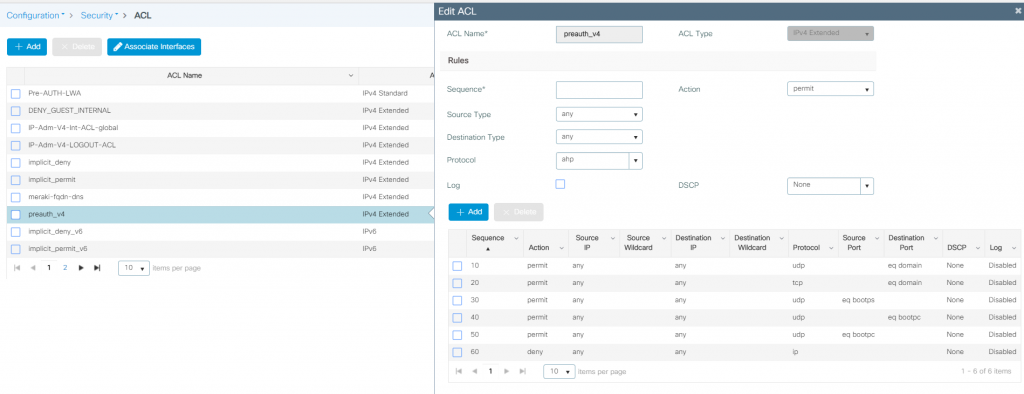
Procedure
| 1 | Choose Configuration > Security > Web Auth. |
| 2 | In the Webauth Parameter Map tab, click the parameter map name. The Edit WebAuth Parameter window is displayed. |
| 3 | In the General tab and choose the required Banner Type: If you choose Banner Text, enter the required banner text to be displayed. If you choose File Name, specify the path of the file from which the banner text has to be picked up. |
| 4 | Click Update & Apply. |
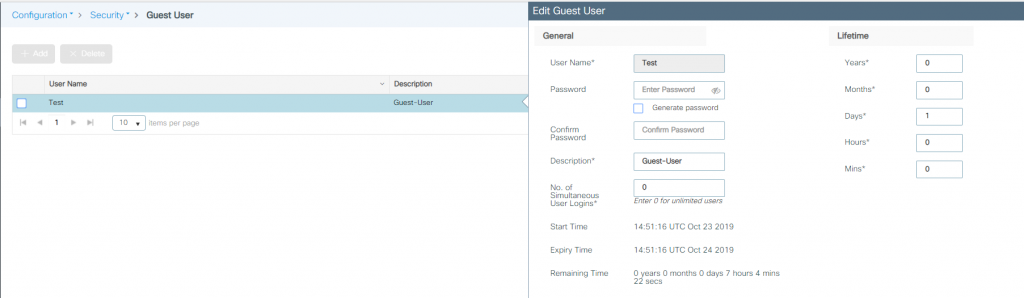
What was not covered in the Cisco guide was how to add a guest user. To create a new guest user:
Navigate to Configuration > Security > Guest User:
Now we have everything configured and a guest user account set up we are ready to connect to the guest LWA WLAN – Woohoo!
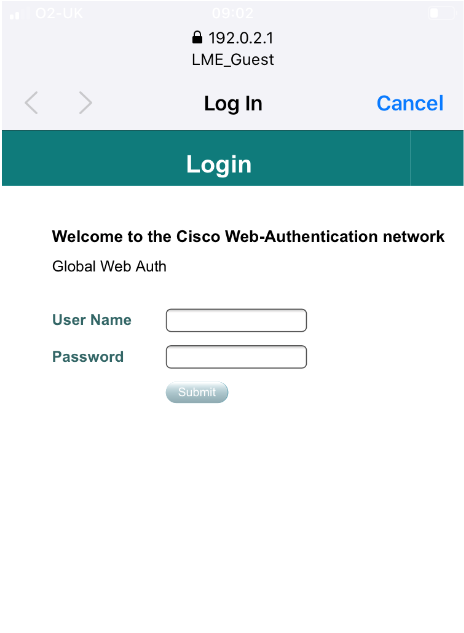
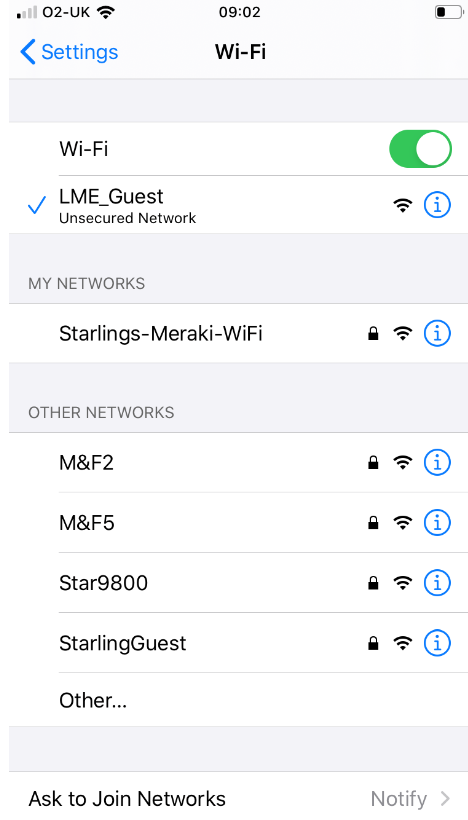
Successfully connected client via LWA and anchored to the anchor WLC from the foreign WLC:
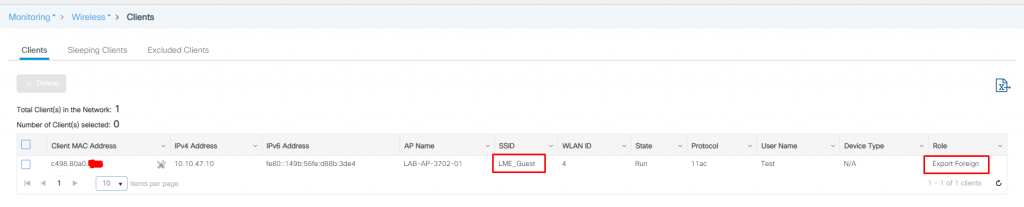
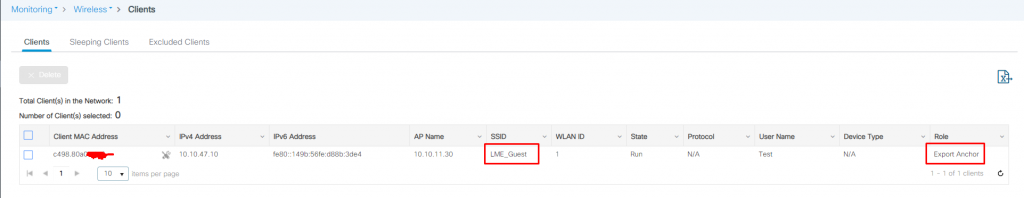
Successfully connected client via LWA and anchored on anchor WLC:
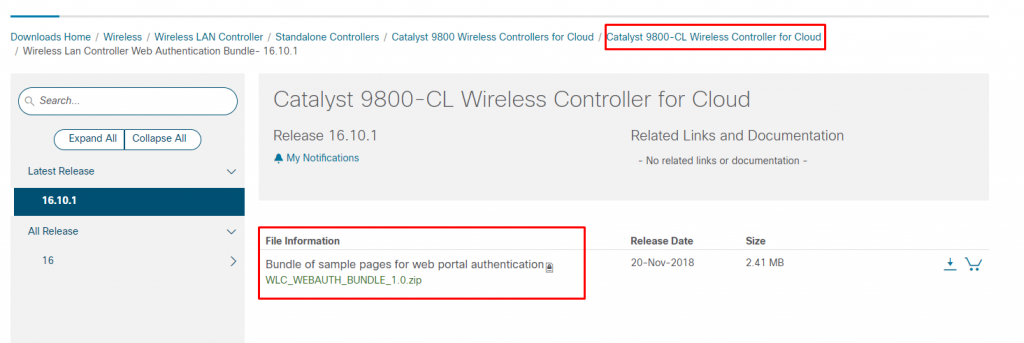
I was just using the default captive portal in my lab – if you or your customer would like to customise the captive portal here is the Cisco guide and a screenshot of where you can download the webauth bundle from Cisco for your C9800! The bundle is very dated and has a proper vintage feel to it but it’s certainly possible to adjust it so it looks OK 🙂
Hopefully, this post helps and saves you guys a bit of time if you need to configure a Local Web Authentication (LWA) WLAN in the future.
As always any feedback or comments are always welcome.
X